Explain Difference Between Asymmetric and Symmetric With Some Use Cases
There are two types of Clustering systems ie. However a major difference is that clustered systems are created by two or more individual computer systems merged together.

Symmetric Vs Asymmetric Encryption What S The Difference
In generally helps to protect private information sensitive data and enhance security.

. We use symmetric key encryption when we need to transfer large chunks of information and data. Asymmetric encryption uses two related keys public and private for data encryption and decryption and takes away the security risk of key sharing. Takes a single parameter that has to be a set and returns a new set.
Asymmetric arthritis affects the joints on just one side of the body. The operating system treats all the processors equally and no processor is reserved for special purposes. This isnt the case.
If a line were drawn dissecting the. Relation R of a set A is antisymmetric if ab R and ba R then ab. Please explain the differences between the symmetric encryption model and the asymmetric encryption paradigm.
Asymmetric and symmetric clustering systems. To understand why this is the case its necessary to understand a little bit about how each encryption technology works. There are inherent challenges with symmetric key encryption in that the key must somehow be managed.
Logically in any cryptosystem both the keys are closely associated. It uses two different key to encrypt and decrypt the message. In the symmetric division model a stem cell produces two differentiated cells or two stem cells.
For all xy X xy R and x y yx R. In symmetric multiprocessing multiple processors share a common memory and operating system. Clustering systems are similar to parallel systems as they both have multiple CPUs.
However in adverse selection there is a lack. The difference in speed can be significant even into the 100x faster range. Lets look at the Venn diagram of the symmetric_difference between two sets.
Symmetric key algorithms tend to be mathematically simpler and as a result faster. A symmetrical distribution occurs when the values of variables appear at regular frequencies and often the mean median and mode all occur at the same point. Distributing a shared key is a major security risk.
A relation is symmetric if for all xy X xy R yx R. Encryption as name suggests is generally a technique that is used to conceal message using algorithms. There are many other types and.
Solution for Asymmetric and symmetric encryption are two different concepts. The private key is never exposed. It is more secure than symmetric key encryption technique but is much slower.
The stem cells are capable of both symmetric and asymmetric divisions see Figure 1The relative proportion of symmetric divisions can vary and is denoted by the symbol see Table 1 where means that all divisions are symmetrical and means that stem. It is fundamental application of cryptography that encodes a message with an algorithm. In the asymmetric division model a stem cell produces one differentiated cell and one stem cell.
It is practically impossible to decrypt the ciphertext with the key that is unrelated to the encryption key. Symmetric arthritis affects the same joints on both sides of the body such as knees or wrists. The main difference is when it occurs.
If there are a set_A and set_B then the symmetric difference between them will be equal to the union of set_A and set_B without the intersection between the two. Relation R on a set A is asymmetric if abR but ba R. A relation is antisymmetric if.
For all xy X xy R and yx R x y. The main difference between these cryptosystems is the relationship between the encryption and the decryption key. It ensures non-repudiation authenticity added to confidentiality.
We consider a two-compartment agent-based model of stem cells and transit-amplifying TA cells. So why then is there a recommendation to use symmetric keys to encrypt data. We need to check for the given code if the unit test is appropriate for the given case.
Many of the functions used within the Windows 2000 implementation of public key encryption use both public key and symmetric key encryption algorithms. A relation is asymmetric if for all xy X xy R yx R. Asymmetric or Symmetric.
In other words all the processors have common sharedcommon memory and same data path or IO bus as shown in the figure. Uncovering division patterns of stem cells has been subject of intense research in the last fifteen years. It is much faster and provides confidentiality for large chunks of data.
Asymmetric and Symmetric Clustering System. Symmetric multiprocessing refers to the computer architecture where multiple identical processors are interconnected to a single shared main memory with full accessibility to all the IO devices unlike asymmetric MP. Relation R on set A is symmetric if b aR and abR.
Symmetric Difference is marked in Green. All of these processors work in tandem to execute processes. It only requires a single key for both encryption and decryption.
We use asymmetric key encryption when we need to transfer only very small amounts of data. In a moral hazard situation the change in the behavior of one party occurs after the agreement has been made. Is equal to is a symmetric relation such as 3.
Difference between Encryption and Cryptography. Please explain the difference between the two. Asymmetric Multiprocessor System.
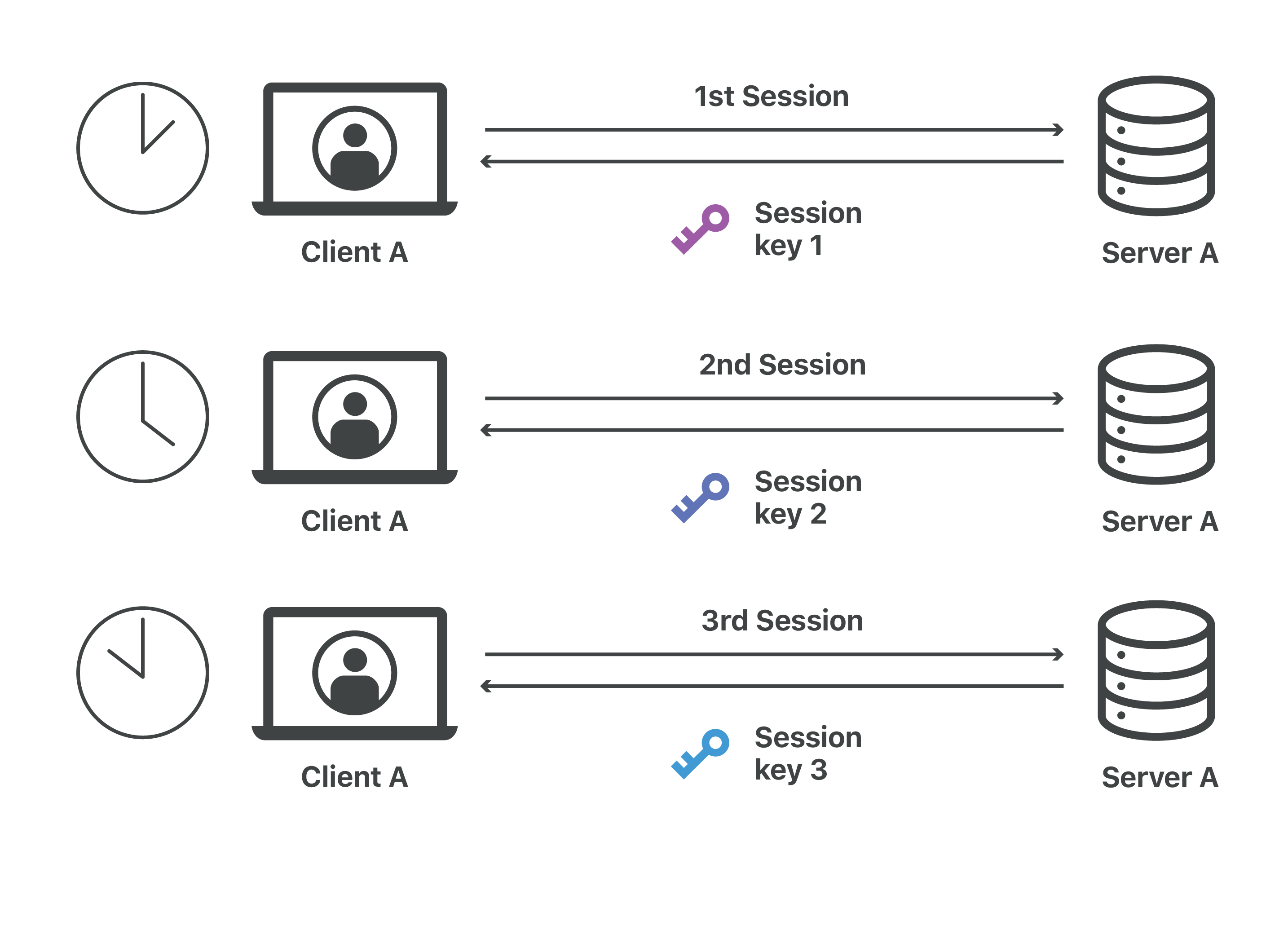
What Is A Session Key Session Keys And Tls Handshakes Cloudflare

All About Ssl Cryptography Digicert Com Cryptography Encryption Algorithms Ssl
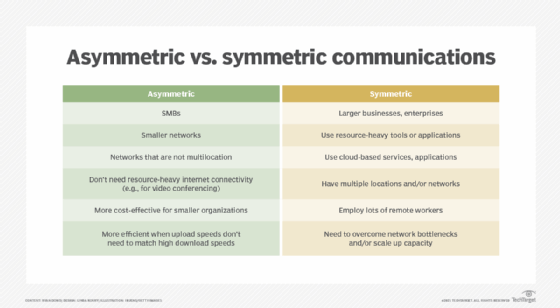
What Is Asymmetric Communications And How Does It Work
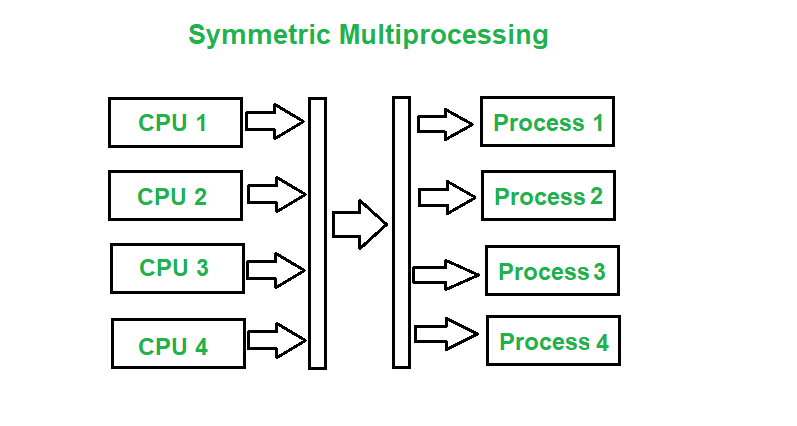
Difference Between Asymmetric And Symmetric Multiprocessing Geeksforgeeks

Symmetry In Diverse Flower Shapes A Asymmetrical Flowers Have No Download Scientific Diagram
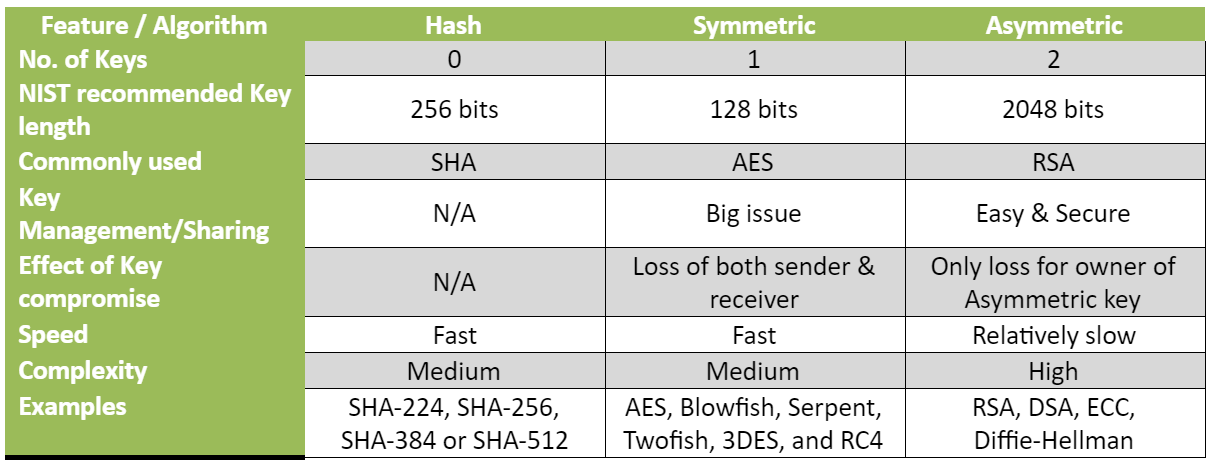
Differences Between Hash Functions Symmetric Asymmetric Algorithms
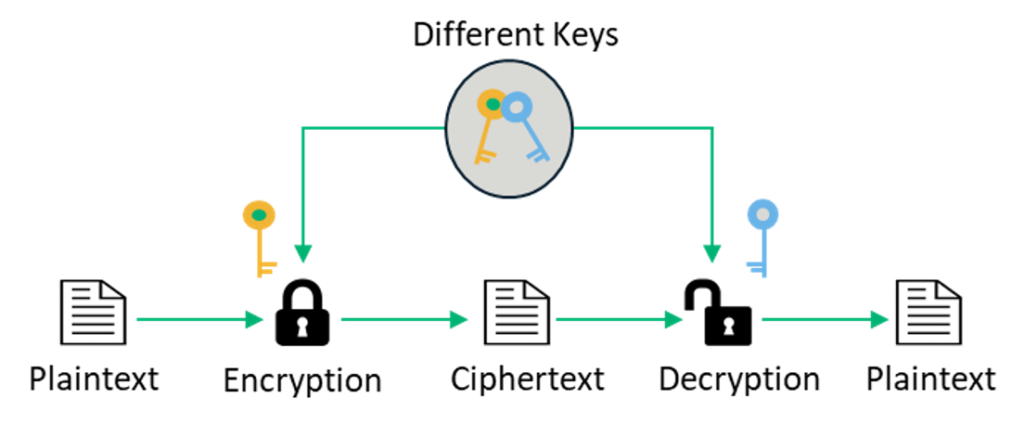
Symmetric Vs Asymmetric Encryption 5 Differences Explained By Experts
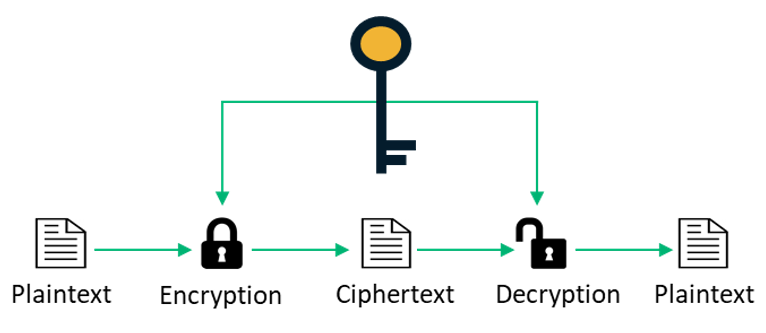
Symmetric Vs Asymmetric Encryption 5 Differences Explained By Experts

What Is Cryptography Symmetric Asymmetric Hashing Encryption Consulting
Encryption Symmetric Encryption Vs Asymmetric Encryption Cryptography Practical Tls Youtube

What Is A Session Key And How Does It Work

Symmetric Vs Asymmetric Encryption Binance Academy In 2021 Encrypted Messages Encryption Algorithms Symmetric Cryptography
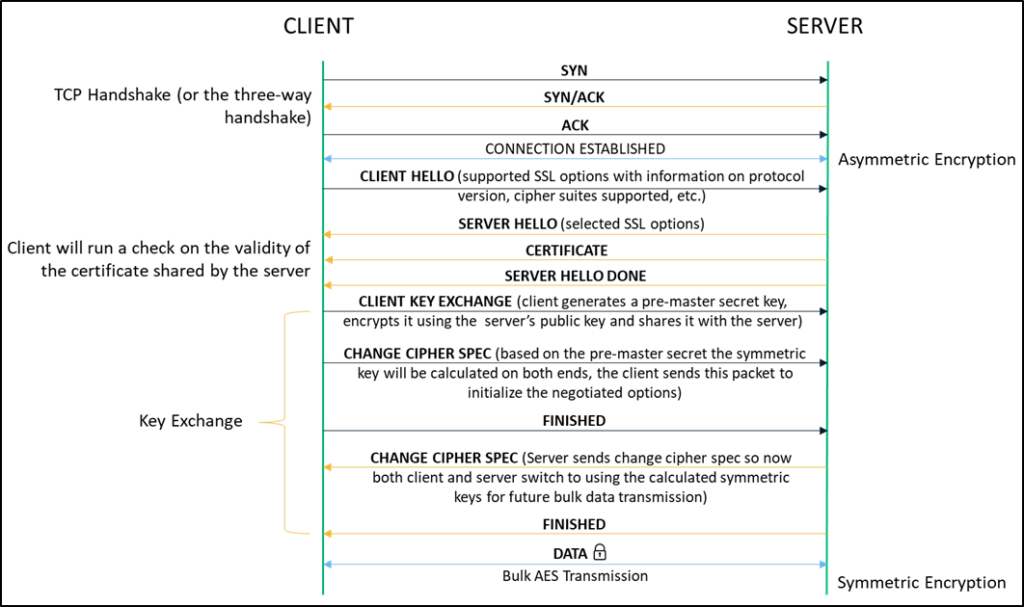
Symmetric Vs Asymmetric Encryption 5 Differences Explained By Experts

What Is Symmetric Key Cryptography Encryption Security Wiki
Symmetric Vs Asymmetric Encryption What Are The Difference
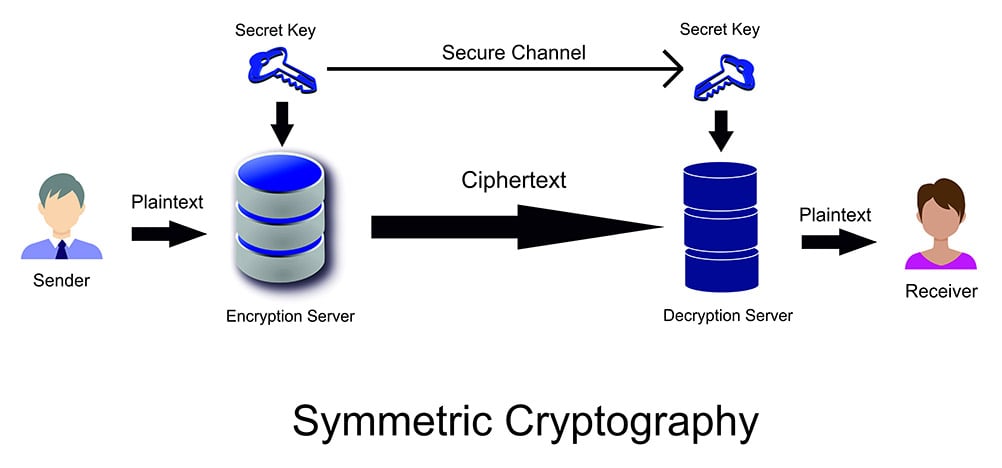
Symmetric Vs Asymmetric Encryption What S The Difference
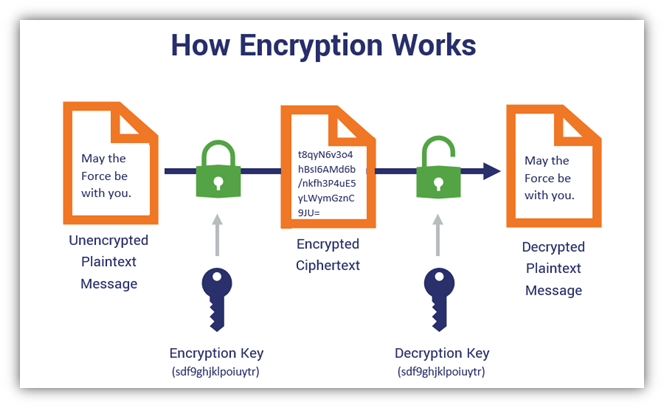
Symmetric Encryption 101 Definition How It Works When It S Used Security Boulevard
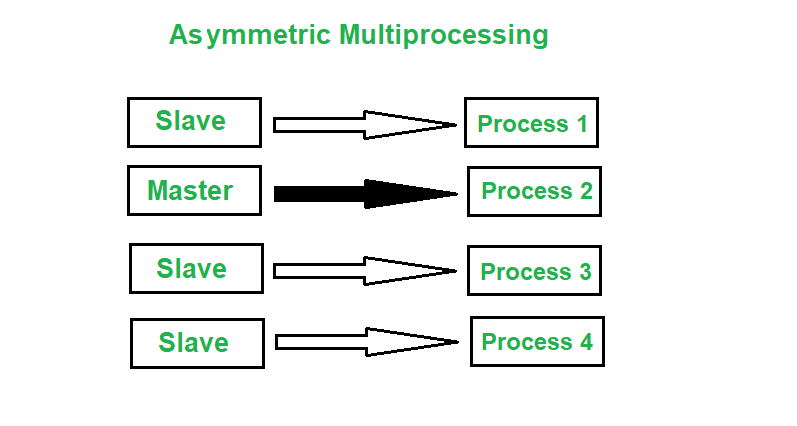
Difference Between Asymmetric And Symmetric Multiprocessing Geeksforgeeks
